A computer malware that has spread
across 150 countries appears to be slowing down, with few reports of
fresh attacks in Asia and Europe on Monday.
However staff beginning the working week have been told to be careful.
The WannaCry ransomware started taking over users' files on Friday, demanding $300 (£230) to restore access.
Hundreds
of thousands of computers have been affected so far. Computer giant
Microsoft said the attack should serve as a wake-up call.
BBC
analysis of three accounts linked to the ransom demands suggests only
about $38,000 (£29,400) had been paid by Monday morning.
However, the ransomware warning said that the cost would double after three days, so the payments may increase.
It threatens to delete files within seven days if no payment is made.
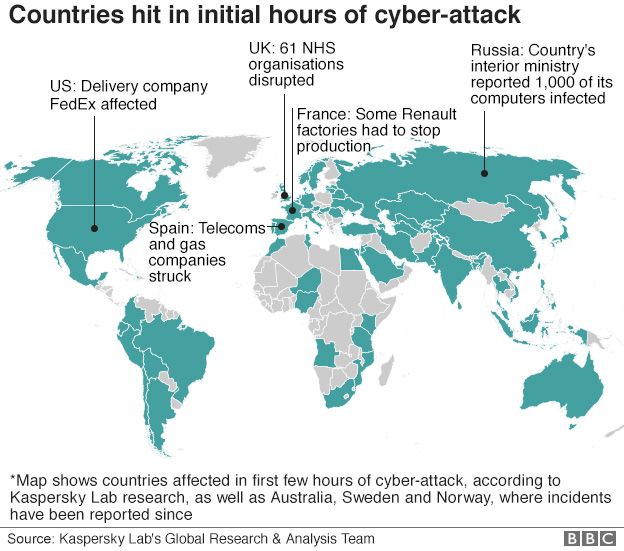
Among the organisations targeted worldwide have been Germany's rail
network Deutsche Bahn, Spanish telecommunications operator Telefonica,
US logistics giant FedEx and Russia's interior ministry.
Demo how the infection would be like?
How has Monday been so far?
Many firms employed experts over the weekend to try to prevent new infections.
The picture now appears better in Europe.
Senior
spokesman for Europol, Jan Op Gen Oorth, told the AFP news agency: "The
number of victims appears not to have gone up and so far the situation
seems stable in Europe, which is a success.
"It seems that a lot of internet security guys over the weekend did their homework and ran the security software updates."
UK Health Minister Jeremy Hunt confirmed to the BBC that UK intelligence services had found no evidence of a second wave of attacks on Monday.
The
UK's National Crime Agency earlier tweeted: "We haven't seen a second
spike in WannaCry ransomware attacks, but that doesn't mean there won't
be one."
The badly affected National Health Service said seven out of 47 trusts that were hit were still facing serious issues.
French carmaker Renault said its plant in the northern town of Douai
would not reopen on Monday as it dealt with the cyber-attack.
In Asia, where offices closed before the ransomware struck on Friday, the spread was reportedly slowing:
- Australia: At least eight businesses reported being locked out of their systems
- South Korea: Four companies reported problems over the weekend. One cinema chain was unable to display trailers
- Indonesia: Records at two hospitals were blocked
- Japan: Both Nissan and Hitachi reported some units had been affected, but not seriously
- China: Hundreds of thousands of computers suffered initially, China's Qihoo tech firm said. Universities, with older systems, were particularly badly hit. Some payment systems and government services affected, but less than feared
Banking systems across the region were largely unaffected.
Who is behind the attack?
This
won't take long. Nobody knows. Europol's Jan Op Gen Oorth said: "A bit
early to say... but we are working on a decrypting tool".
Associated
Press quoted Tim Wellsmore, of US security firm FireEye, as saying: "We
expect this is a small operation... They just happened to hit the
mother lode."
Russian President Vladimir Putin said: "Russia has absolutely nothing to do with it."
Should people pay?
Companies in Asia and Europe have been warning employees to be careful when clicking on attachments and links in their emails.
The message from the UK's National Crime Agency was "do not pay!" - there is no guarantee that systems will be restored.
Michael
Gazeley, of Network Box, a Hong Kong-based cyber-security firm, told
Reuters there were still "many 'landmines' waiting in people's inboxes",
adding that his firm had detected a new version that infected users
directly via a malicious link on hacked websites.
Becky Pinkard, from Digital Shadows, a UK-based cyber-security firm,
also said it would be easy for the initial attackers or "copy-cat
authors" to change the virus code so it is difficult to guard against.
A
UK security researcher known as "MalwareTech", who helped to limit the
ransomware attack, predicted "another one coming... quite likely on
Monday".
MalwareTech, whose name was revealed in UK media to be
22-year-old Marcus Hutchins, was hailed as an "accidental hero" after
registering a domain name to track the spread of the virus, which
actually ended up halting it.
What's behind Microsoft's 'wake-up call' warning?
The computing giant says the tool used in this current attack had been developed by the US National Security Agency and was stolen by hackers.
It is highly critical of the way governments store data on software vulnerabilities.
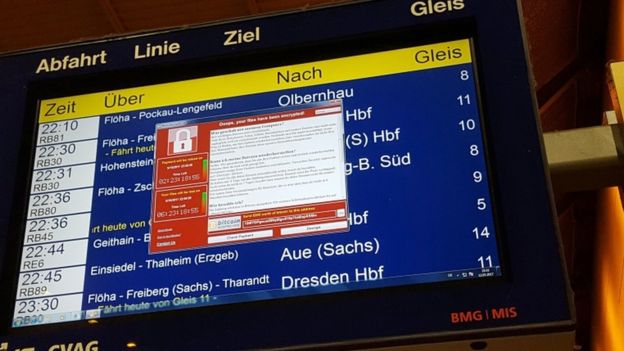
A railway station system in Chemnitz, eastern Germany, is infected
Microsoft president and chief legal officer Brad Smith said on
Sunday: "We have seen vulnerabilities stored by the CIA show up on
Wikileaks, and now this vulnerability stolen from the NSA has affected
customers around the world.
"An equivalent scenario with conventional weapons would be the US military having some of its Tomahawk missiles stolen."
The organisation also said that many organisations had failed to keep their systems up to date, allowing the virus to spread.
Microsoft
said it had released a Windows security update in March to tackle the
problem involved in the latest attack, but many users were yet to run
it.
Analysis: Dave Lee, BBC North America technology reporter
There
are going to be some tough questions on Monday for those institutions
which didn't do enough to keep their networks secure, as well as the
organisations that were best placed to stop it happening in the first
place - the NSA and Microsoft.
The NSA keeps a chest of
cyber-weapons to itself so it can hit targets, but Microsoft has long
argued that this is dangerous. If there is a flaw in Windows, the
company said, surely the safest thing to do is to let its team know
straight away so it can be fixed.
But then Microsoft also needs to
consider what obligation it has to update all users - not just the ones
who pay extra for security on older systems.
Updating your
computer if you're an individual is a piece of cake, but for a network
the size of Britain's National Health Service? Tough - time-consuming,
expensive and complex.



